Cryptanalysis 2 (by alaric)
I've still yet to analyze the wider algorithm I suggested in the last post:
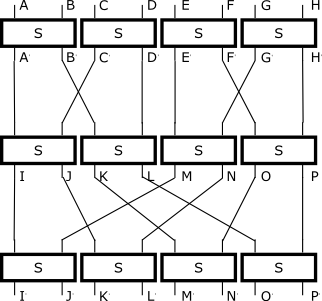 * Input ABCDEFGH
* A'B'=S(AB), C'D'=S(CD), E'F'=S(EF), G'H'=S(GH)
* IJ=S(A'C'), KL=S(B'D'), MN=S(E'G'), OP=S(F'H')
* I'J'=S(IM), K'L'=S(JN), M'N'=S(KO), O'P'=S(LP)
* Output I'J'K'L'M'N'O'P'
* Input ABCDEFGH
* A'B'=S(AB), C'D'=S(CD), E'F'=S(EF), G'H'=S(GH)
* IJ=S(A'C'), KL=S(B'D'), MN=S(E'G'), OP=S(F'H')
* I'J'=S(IM), K'L'=S(JN), M'N'=S(KO), O'P'=S(LP)
* Output I'J'K'L'M'N'O'P'
But another to try, considering the success I had with the avalanche function on an 8-bit S-box, is the one I suggested back in the avalanche function post - break a block into an arbitrary number of 16-bit subblocks, pass each through the same S-box, then run an 8-bit avalanche function across the result, then another row of 16-bit S-boxes, then repeat the last two steps a few times.
